SEE Class 10 –COMPUTER SCIENCE Model Question Solutions (SET 5)
RE-3031
Group ‘A’
1. Answer the following questions in one sentence:
a) What is unguided media?
Unguided media is a communication channel in which data and information are transferred through the air using electromagnetic waves, such as radio waves or microwaves, without using wire or cable.
b) What is the business done through the mobile?
The business done through the mobile is M-Commerce
c) Which data type is used to store the date of birth in MS Access?
Date/Time is the data type is used to store date of birth in MS Access
d) Write any two elements of the database.
Field and Record are the two elements of the database
e) What is modular programming?
Modular programming is a technique used to divide program into many small logical, manageable and functional modules or blocks
f) Write any two features of C- language.
· Portability: C code can be compiled and executed on different systems with minimal modifications.
· C is a case-sensitive programming language. It understands the capital alphabets and small alphabets as different values.
2. Write appropriate technical term for the following:
a) A secret group of characters used to protect computer system from unauthorized users. Password
b) An artificial environment created by a computer system that appears real. Virtual reality
3. Write the full form of the following
a) URL – Uniform Resource Locator
b) STP – Shielded Twisted Pair Cable
4. Answer the following questions:
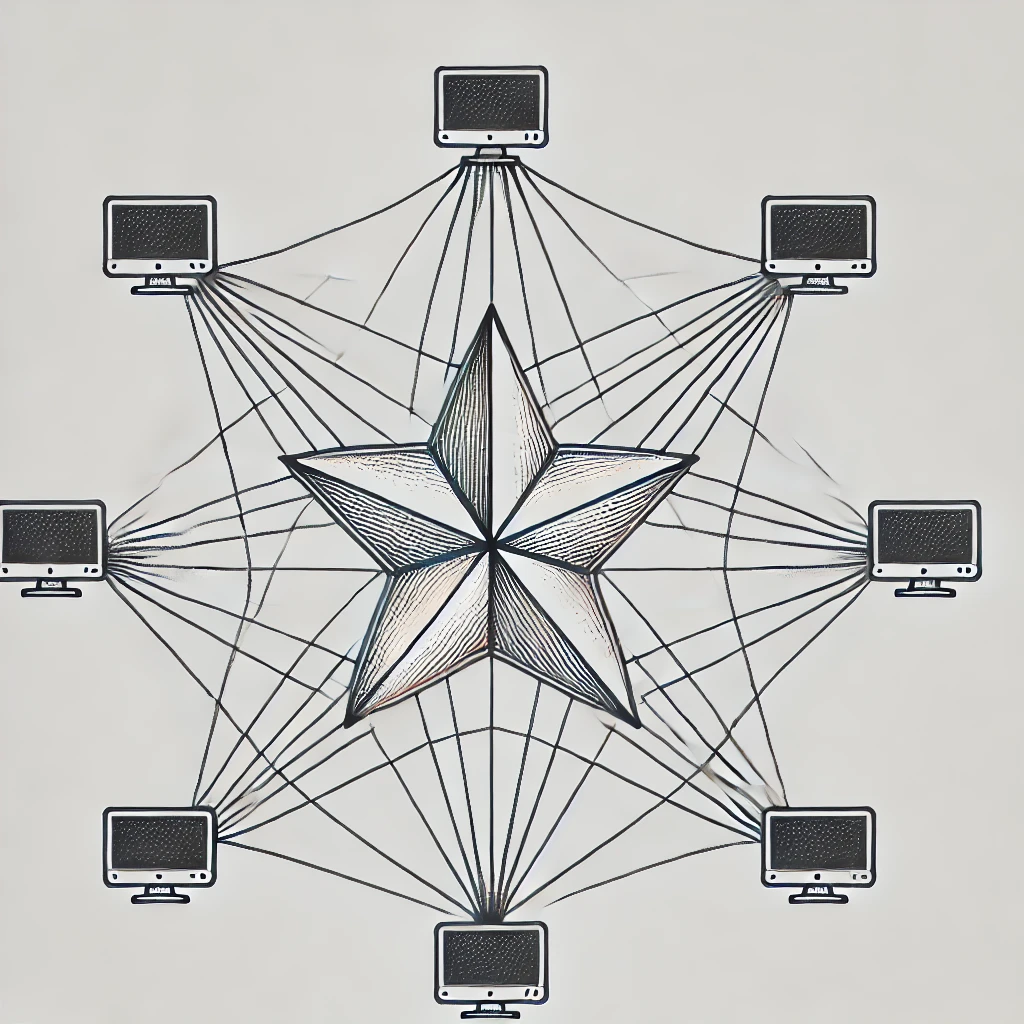
a) Define network topology. Sketch a drawing of star topology.
Network topology is the inter-connected pattern of network components.
b) Write any four commandments of computer ethics.
- Do not use a computer to publish fake information.
- Do not search the file or record of other people.
- Do not destroy or delete the records of other people.
- Do not use a computer to steal someone’s privacy.
c) What are the computer security threats? Mention any two measures to protect from security threats.
Computer security threat is a risk which can potentially harm computer systems and organization.
Any two measures to protect from security threats are: Firewall and Cryptography
d) What is E-commerce? List any two E-commerce companies in Nepal.
E-commerce refers to buying and selling of goods, products or services through Internet.
Any two E-commerce companies in Nepal are sastodeal and daraz
e) Define Artificial Intelligence with examples.
Artificial Intelligence (AI) is the simulation of human intelligence in machines that are programmed to think and learn like humans.
Examples are self-driving cars, speech recognition (Siri) , face recognition, etc.
f) List any four features of MS Access.
- It provides flexible ways to add, edit, delete, and display the related data.
- Queries help to view, change, and analyze the data in different ways.
- Forms are used for viewing and editing the information.
- Reports are used for summarizing and printing the data.
g) What is the Primary Key? Give any two benefits of it.
A primary key is a unique field in a database table that identifies each record uniquely.
Any two benefits of the primary key are:
- It sets the relationship between tables.
- It reduces and controls the duplication of records in a table
h) Give the differences between the Select Query and Action Query.
| Select Query | Action Query |
| Select query is simply used to select and display the relevant data from the database. | An action query is a query that makes changes to or removes many records in just one operation. |
| It does not make change to database. | It does not make changes to the database. |
i) Identify a record and field from the following table structure:
| Symbol No. | Name | Marks |
| 00100202S | Aarambha Shrestha | 91 |
| 00100203T | Suhisha Rayamajhi | 99 |
Field = Symbol No. , Name and Marks
Record 1 = 001002020S, Aarambha Shrestha, 91
Record 2 = 00100203T, Suhisha Rayamajhi, 99
5. Write down the output of the given program and show them in dry run table:
DECLARE FUNCTION SQN (N)
CLS
S=0
FOR L=1 TO 3
READ NUM
S=S+SQN (NUM)
NEXT L
PRINT “Sum of square”; S
DATA 1, 4, 5
END
FUNCTION SQN (N)
SQN = N^2
END FUNCTION
Dry Run
| S | L=1 TO 3 | Read Num | S=S+SQN(NUM) | SQN=N^2 |
| 0 | 1 TO 3 yes | 1 | 0+1=1 | 1^2=1 |
| 17 | 2 TO 3 yes | 4 | 1+16=17 | 4^2=16 |
| 42 | 3 TO 3 yes | 5 | 17+25=42 | 5^2=25 |
| 4 TO 3 No Loop Exits |
The output of the program is :
Sum of square 42
6. Re-Write the given program after correcting the bugs:
DECLARE SUB Square (A)
REM to print square of a input number
CLS
GET “Enter a number”; N
Square (N)
END
SUB Square (A)
Sq = A^ 4
Display “Square of a number is “; Sq
End Sub
Debugged Program
DECLARE SUB Square (A)
REM to print square of a input number
CLS
INPUT “Enter a number”; N
CALL Square (N)
END
SUB Square (A)
Sq = A^ 2
PRINT “Square of a number is “; Sq
End SUB
7. Study the following program and answer the given questions:
DECLARE FUNCTION Count (W$)
INPUT “Enter a word”; R$
C = Count (R$)
PRINT C
END
FUNCTION Count (W$)
FOR L = 1 TO LEN (W$)
Ch$MID$ (W$, L, 1)
IF UCASES (Ch$) = “K” THEN
N=N+1
END IF
NEXT L
Count = N
END FUNCTION
a) List any two library functions used in the above program.
UCASE$( ) and MID$( ) are the two library functions used in the above program
b) Write the use of variable ‘C’ in line 3 [i.e. C = Count (R$)] given in the above program.
The use of variable ‘C’ in line 3 [i.e. C = Count (R$)] given in the above program is to store the value returned by the function count( ).
Group ‘C’
8. Convert/Calculate as per the instruction:
a) (ABC)16 = (?)8
Convert each hex digit to 4 binary digits
ABC
= A B C
A = 1010
B = 1011
C = 1100
= 101010111100
Convert every 3 binary digits (from bit0) to octal digit
101010111100
= 101 010 111 100
101 = 5
010 = 2
111 = 7
100 = 4
= 5274
(ABC)16 = (5274)8
b) (435)10 = (?)2
| Division by 2 | Quotient | Remainder(Digit) |
| (435)/2 | 217 | 1 |
| (217)/2 | 108 | 1 |
| (108)/2 | 54 | 0 |
| (54)/2 | 27 | 0 |
| (27)/2 | 13 | 1 |
| (13)/2 | 6 | 1 |
| (6)/2 | 3 | 0 |
| (3)/2 | 1 | 1 |
| (1)/2 | 0 | 1 |
= (110110011)2
(435)10 = (110110011)2
iii) (101)2x (101)2=(?)2
| 1 | 0 | 1 | |||
| X | 1 | 0 | 1 | ||
| 1 | 0 | 1 | |||
| 0 | 0 | 0 | X | ||
| + | 1 | 0 | 1 | X | X |
| 1 | 1 | 0 | 0 | 1 |
(101)2x (101)2=(11001)2
iv) (101101) /¸(101)
| 101) | 1 | 0 | 1 | 1 | 0 | 1 | (1001 | |
| – | 1 | 0 | 1 | |||||
| 0 | 0 | 0 | 1 | 0 | 1 | |||
| – | 1 | 0 | 1 | |||||
| 0 | 0 | 0 | ||||||
Quotient = 1001
Remainder = 0
9a) Write a program in QBASIC that asks length, breadth and height of room and calculate its area and volume. Create a User Defined Function to calculate Area and Sub Program to calculate the Volume.
[Hint: Area LxB and Volume = LxBxH]
DECLARE FUNCTION AREA(L,B)
DECLARE SUB VOL(L,B,H)
CLS
INPUT “Enter Length”; L
INPUT “Enter Breadth”; B
INPUT “Enter Height”; H
PRINT “Area of room=”; AREA(L,B)
CALL VOL(L,B,H)
END
FUNCTION AREA(L,B)
AREA = L * B
END FUNCTION
SUB VOL(L,B,H)
V=L*B*H
PRINT “Volume of Room=”; V
END SUB
b) Employee’s name, address, gender and salary are stored in the “EMP.DAT” sequential data file. Write a QBASIC program that displays all information about personnel whose salaries exceed 60000.
OPEN “EMP.DAT” FOR INPUT AS #1
CLS
WHILE NOT EOF (1)
INPUT #1, N$, A$, G$, S
IF S > 60000 THEN PRINT N$, A$, G$, S
WEND
CLOSE #1
END
10. Write a program in ‘C’ language to find simple interest where user need to input Principle, Rate and Time.
#include<stdio.h>
#include<conio.h>
int main()
{
float p, t, r, i;
printf(“Enter principal: “);
scanf(“%f”, &p);
printf(“Enter time: “);
scanf(“%f”, &t);
printf(“Enter rate: “);
scanf(“%f”, &r);
i = (p*t*r)/100;
printf(“Simple Interest = %.2f”, i);
return 0;
}
(Or)
Write a program in ‘C’ language to display the series with their sum. 1,2,3,4, up to 10th term.
#include <stdio.h>
int main()
{
int i,s=0;
for(i=1;i<=10;i++)
{
printf(“%d “,i);
s=s+i;
}
printf(“\n Sum =%d”,s);
return 0;
}

